- A+
docker容器网络配置
Docker在安装后自动提供3种网络,可以使用docker network ls命令查看
[root@localhost ~]# docker network ls NETWORK ID NAME DRIVER SCOPE bca5c00311b4 bridge bridge local 53aa6b51eb52 host host local d9b9ada86204 none null local Docker使用Linux桥接,在宿主机虚拟一个Docker容器网桥(docker0),Docker启动一个容器时会根据Docker网桥的网段分配给容器一个IP地址,称为Container-IP,同时Docker网桥是每个容器的默认网关。因为在同一宿主机内的容器都接入同一个网桥,这样容器之间就能够通过容器的Container-IP直接通信。
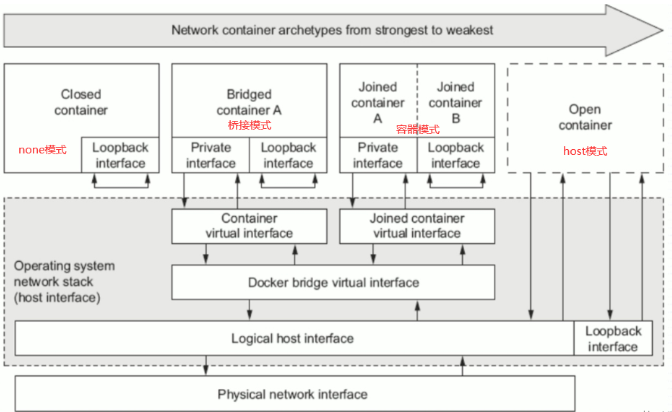
docker的4种网络模式
| 网络模式 | 配置 | 说明 |
|---|---|---|
| host | --network host | 容器和宿主机共享Network namespace |
| container | --network container:NAME_OR_ID | 容器和另外一个容器共享Network namespace |
| none | --network none | 容器有独立的Network namespace, 但并没有对其进行任何网络设置, 如分配veth pair 和网桥连接,配置IP等 |
| bridge | --network bridge | 默认模式 |
[root@localhost ~]# docker pull busybox Using default tag: latest latest: Pulling from library/busybox 5cc84ad355aa: Pull complete Digest: sha256:5acba83a746c7608ed544dc1533b87c737a0b0fb730301639a0179f9344b1678 Status: Downloaded newer image for busybox:latest docker.io/library/busybox:latest [root@localhost ~]# docker pull httpd Using default tag: latest latest: Pulling from library/httpd a2abf6c4d29d: Pull complete dcc4698797c8: Pull complete 41c22baa66ec: Pull complete 67283bbdd4a0: Pull complete d982c879c57e: Pull complete Digest: sha256:0954cc1af252d824860b2c5dc0a10720af2b7a3d3435581ca788dff8480c7b32 Status: Downloaded newer image for httpd:latest docker.io/library/httpd:latest [root@localhost ~]# docker images REPOSITORY TAG IMAGE ID CREATED SIZE busybox latest beae173ccac6 7 months ago 1.24MB httpd latest dabbfbe0c57b 7 months ago 144MB //拉取镜像并列出查看 bridge模式
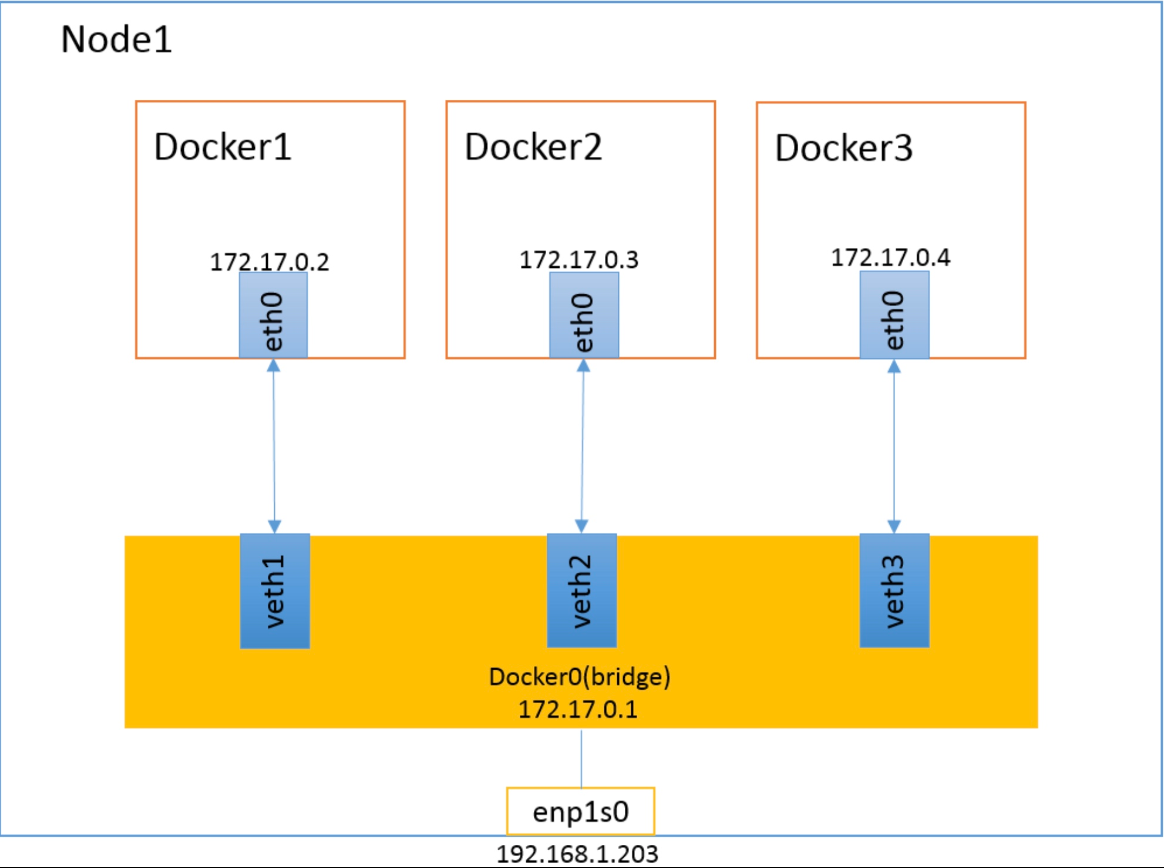
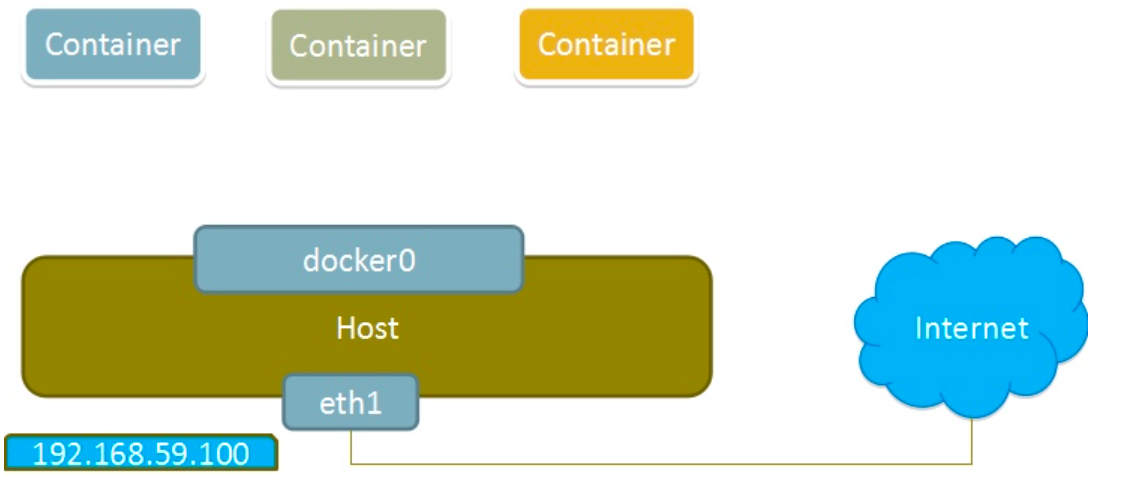
当Docker进程启动时,会在主机上创建一个名为docker0的虚拟网桥,此主机上启动的Docker容器会连接到这个虚拟网桥上。虚拟网桥的工作方式和物理交换机类似,这样主机上的所有容器就通过交换机连在了一个二层网络中。
从docker0子网中分配一个IP给容器使用,并设置docker0的IP地址为容器的默认网关。在主机上创建一对虚拟网卡veth pair设备,Docker将veth pair设备的一端放在新创建的容器中,并命名为eth0(容器的网卡),另一端放在主机中,以vethxxx这样类似的名字命名,并将这个网络设备加入到docker0网桥中。可以通过brctl show命令查看。
bridge模式是docker的默认网络模式,不写--network参数,就是bridge模式。使用docker run -p时,docker实际是在iptables做了DNAT规则,实现端口转发功能。可以使用iptables -t nat -vnL查看。
bridge模式如下图所示:
[root@localhost ~]# docker run -it --network bridge --rm busybox / # ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 4: eth0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever [root@localhost ~]# docker run -it --rm busybox / # ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 6: eth0@if7: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever //创建容器时添加--network bridge与不添加的效果是一样的 container模式
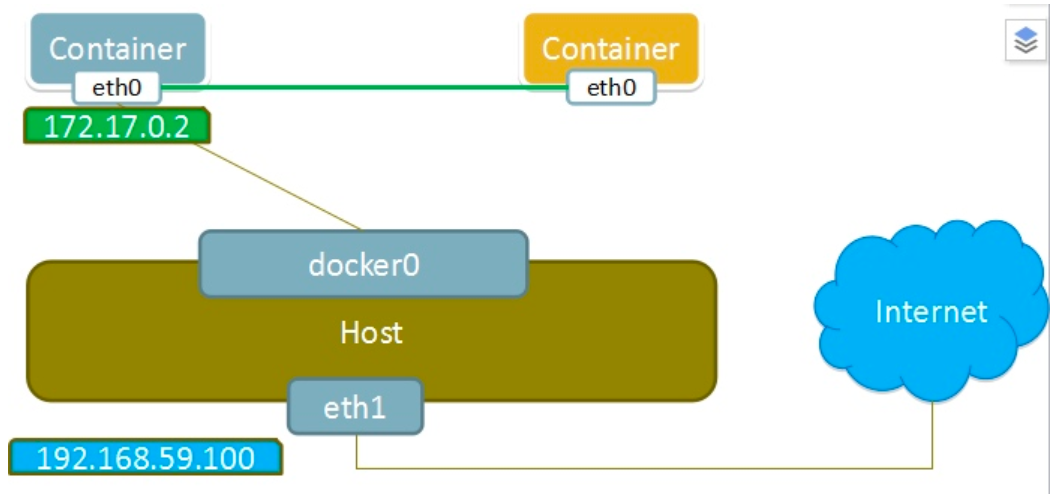
这个模式指定新创建的容器和已经存在的一个容器共享一个 Network Namespace,而不是和宿主机共享。新创建的容器不会创建自己的网卡,配置自己的 IP,而是和一个指定的容器共享 IP、端口范围等。同样,两个容器除了网络方面,其他的如文件系统、进程列表等还是隔离的。两个容器的进程可以通过 lo 网卡设备通信。
container模式如下图所示:
[root@localhost ~]# docker run -it --name b1 --rm busybox / # ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 8: eth0@if9: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever 再开一个终端 [root@localhost ~]# docker run -it --name b2 --rm busybox / # ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 10: eth0@if11: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue link/ether 02:42:ac:11:00:03 brd ff:ff:ff:ff:ff:ff inet 172.17.0.3/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever //新创建的容器和前一个创建的容器ip地址是一样 host模式
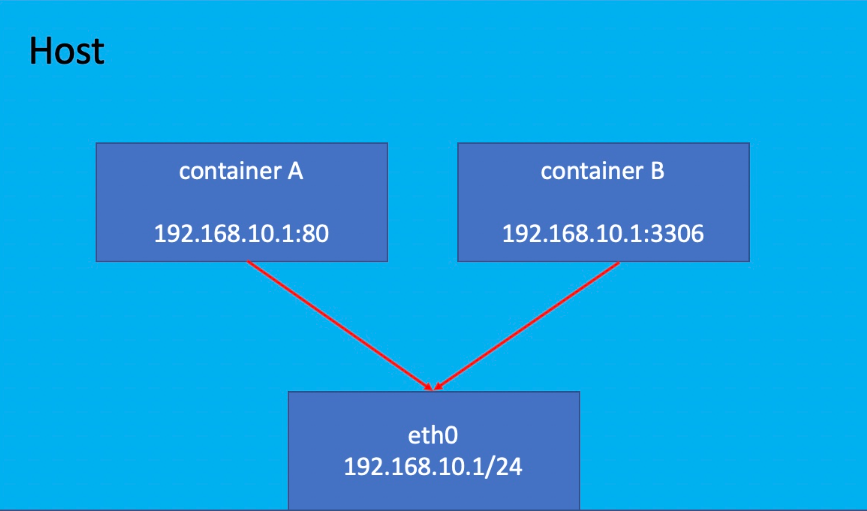
如果启动容器的时候使用host模式,那么这个容器将不会获得一个独立的Network Namespace,而是和宿主机共用一个Network Namespace。容器将不会虚拟出自己的网卡,配置自己的IP等,而是使用宿主机的IP和端口。但是,容器的其他方面,如文件系统、进程列表等还是和宿主机隔离的。
使用host模式的容器可以直接使用宿主机的IP地址与外界通信,容器内部的服务端口也可以使用宿主机的端口,不需要进行NAT,host最大的优势就是网络性能比较好,但是docker host上已经使用的端口就不能再用了,网络的隔离性不好。
Host模式如下图所示:
[root@localhost ~]# docker run -it --name b1 --rm --network host busybox / # ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel qlen 1000 link/ether 00:0c:29:05:f4:28 brd ff:ff:ff:ff:ff:ff inet 192.168.222.250/24 brd 192.168.222.255 scope global noprefixroute ens33 valid_lft forever preferred_lft forever inet6 fe80::20c:29ff:fe05:f428/64 scope link valid_lft forever preferred_lft forever 3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue link/ether 02:42:cf:39:fe:c4 brd ff:ff:ff:ff:ff:ff inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0 valid_lft forever preferred_lft forever inet6 fe80::42:cfff:fe39:fec4/64 scope link valid_lft forever preferred_lft forever none模式
使用none模式,Docker容器拥有自己的Network Namespace,但是,并不为Docker容器进行任何网络配置。也就是说,这个Docker容器没有网卡、IP、路由等信息。需要我们自己为Docker容器添加网卡、配置IP等。
这种网络模式下容器只有lo回环网络,没有其他网卡。none模式可以在容器创建时通过--network none来指定。这种类型的网络没有办法联网,封闭的网络能很好的保证容器的安全性。
应用场景:
启动一个容器处理数据,比如转换数据格式
一些后台的计算和处理任务
none模式如下图所示:
[root@localhost ~]# docker run -it --name b1 --rm --network none busybox / # ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever [root@localhost ~]# docker network inspect bridge [ { "Name": "bridge", "Id": "bca5c00311b41e8db87bc37ef0657fbd36e446d51e55f77ab48223c3d0a7b305", "Created": "2022-08-04T09:11:26.614207143+08:00", "Scope": "local", "Driver": "bridge", "EnableIPv6": false, "IPAM": { "Driver": "default", "Options": null, "Config": [ { "Subnet": "172.17.0.0/16", "Gateway": "172.17.0.1" } ] }, "Internal": false, "Attachable": false, "Ingress": false, "ConfigFrom": { "Network": "" }, "ConfigOnly": false, "Containers": {}, "Options": { "com.docker.network.bridge.default_bridge": "true", "com.docker.network.bridge.enable_icc": "true", "com.docker.network.bridge.enable_ip_masquerade": "true", "com.docker.network.bridge.host_binding_ipv4": "0.0.0.0", "com.docker.network.bridge.name": "docker0", "com.docker.network.driver.mtu": "1500" }, "Labels": {} } ] #查看bridge网络的详细配置 Linux内核实现名称空间的创建
ip netns命令
可以借助ip netns命令来完成对 Network Namespace 的各种操作。ip netns命令来自于iproute安装包,一般系统会默认安装,如果没有的话,请自行安装。
注意:ip netns命令修改网络配置时需要 sudo 权限。
可以通过ip netns命令完成对Network Namespace 的相关操作,可以通过ip netns help查看命令帮助信息:
[root@localhost ~]# ip netns help Usage: ip netns list ip netns add NAME ip netns attach NAME PID ip netns set NAME NETNSID ip [-all] netns delete [NAME] ip netns identify [PID] ip netns pids NAME ip [-all] netns exec [NAME] cmd ... ip netns monitor ip netns list-id [target-nsid POSITIVE-INT] [nsid POSITIVE-INT] NETNSID := auto | POSITIVE-INT 默认情况下,Linux系统中是没有任何 Network Namespace的,所以ip netns list命令不会返回任何信息。
创建Network Namespace
通过命令创建一个名为ns0的命名空间:
[root@localhost ~]# ip netns list [root@localhost ~]# ip netns add ns0 [root@localhost ~]# ip netns list ns0 新创建的 Network Namespace 会出现在/var/run/netns/目录下。如果相同名字的 namespace 已经存在,命令会报Cannot create namespace file "/var/run/netns/ns0": File exists的错误。
[root@localhost ~]# ls /var/run/netns/ ns0 [root@localhost ~]# ip netns add ns0 Cannot create namespace file "/var/run/netns/ns0": File exists 对于每个 Network Namespace 来说,它会有自己独立的网卡、路由表、ARP 表、iptables 等和网络相关的资源。
操作Network Namespace
ip命令提供了ip netns exec子命令可以在对应的 Network Namespace 中执行命令。
查看新创建 Network Namespace 的网卡信息
[root@localhost ~]# ip netns exec ns0 ip addr 1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 可以看到,新创建的Network Namespace中会默认创建一个lo回环网卡,此时网卡处于关闭状态。此时,尝试去 ping 该lo回环网卡,会提示Network is unreachable
[root@localhost ~]# ip netns exec ns0 ping 127.0.0.1 connect: Network is unreachable 通过下面的命令启用lo回环网卡:
[root@localhost ~]# ip netns exec ns0 ip link set lo up [root@localhost ~]# ip netns exec ns0 ping 127.0.0.1 PING 127.0.0.1 (127.0.0.1) 56(84) bytes of data. 64 bytes from 127.0.0.1: icmp_seq=1 ttl=64 time=0.028 ms 64 bytes from 127.0.0.1: icmp_seq=2 ttl=64 time=0.056 ms 64 bytes from 127.0.0.1: icmp_seq=3 ttl=64 time=0.518 ms 64 bytes from 127.0.0.1: icmp_seq=4 ttl=64 time=0.038 ms 64 bytes from 127.0.0.1: icmp_seq=5 ttl=64 time=0.040 ms ^C --- 127.0.0.1 ping statistics --- 5 packets transmitted, 5 received, 0% packet loss, time 4110ms rtt min/avg/max/mdev = 0.028/0.136/0.518/0.191 ms 转移设备
我们可以在不同的 Network Namespace 之间转移设备(如veth)。由于一个设备只能属于一个 Network Namespace ,所以转移后在这个 Network Namespace 内就看不到这个设备了。
其中,veth设备属于可转移设备,而很多其它设备(如lo、vxlan、ppp、bridge等)是不可以转移的。
veth pair
veth pair 全称是 Virtual Ethernet Pair,是一个成对的端口,所有从这对端口一 端进入的数据包都将从另一端出来,反之也是一样。
引入veth pair是为了在不同的 Network Namespace 直接进行通信,利用它可以直接将两个 Network Namespace 连接起来。
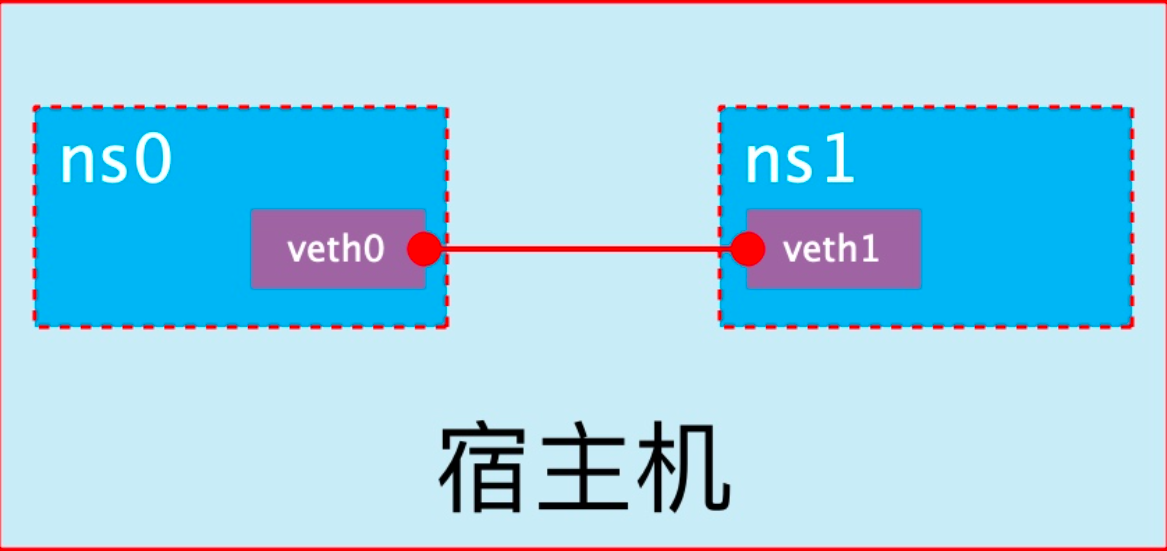
创建veth pair
[root@localhost ~]# ip link add type veth [root@localhost ~]# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 00:0c:29:05:f4:28 brd ff:ff:ff:ff:ff:ff inet 192.168.222.250/24 brd 192.168.222.255 scope global noprefixroute ens33 valid_lft forever preferred_lft forever inet6 fe80::20c:29ff:fe05:f428/64 scope link valid_lft forever preferred_lft forever 3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default link/ether 02:42:cf:39:fe:c4 brd ff:ff:ff:ff:ff:ff inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0 valid_lft forever preferred_lft forever inet6 fe80::42:cfff:fe39:fec4/64 scope link valid_lft forever preferred_lft forever 12: veth0@veth1: <BROADCAST,MULTICAST,M-DOWN> mtu 1500 qdisc noop state DOWN group default qlen 1000 link/ether 16:4f:71:a9:27:41 brd ff:ff:ff:ff:ff:ff 13: veth1@veth0: <BROADCAST,MULTICAST,M-DOWN> mtu 1500 qdisc noop state DOWN group default qlen 1000 link/ether fe:be:d8:2b:86:0c brd ff:ff:ff:ff:ff:ff 可以看到,此时系统中新增了一对veth pair,将veth0和veth1两个虚拟网卡连接了起来,此时这对 veth pair 处于”未启用“状态。
实现Network Namespace间通信
下面我们利用veth pair实现两个不同的 Network Namespace 之间的通信。刚才我们已经创建了一个名为ns0的 Network Namespace,下面再创建一个信息Network Namespace,命名为ns1
[root@localhost ~]# ip netns add ns1 [root@localhost ~]# ip netns list ns1 ns0 然后我们将veth0加入到ns0,将veth1加入到ns1
[root@localhost ~]# ip link set veth0 netns ns0 [root@localhost ~]# ip link set veth1 netns ns1 然后我们分别为这对veth pair配置上ip地址,并启用它们
[root@localhost ~]# ip netns exec ns0 ip link set veth0 up [root@localhost ~]# ip netns exec ns0 ip addr add 192.168.222.111/24 dev veth0 [root@localhost ~]# ip netns exec ns1 ip link set veth1 up [root@localhost ~]# ip netns exec ns1 ip addr add 192.168.222.112/24 dev veth1 查看这对veth pair的状态
[root@localhost ~]# ip netns exec ns0 ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 12: veth0@if13: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 16:4f:71:a9:27:41 brd ff:ff:ff:ff:ff:ff link-netns ns1 inet 192.168.222.111/24 scope global veth0 valid_lft forever preferred_lft forever inet6 fe80::144f:71ff:fea9:2741/64 scope link valid_lft forever preferred_lft forever [root@localhost ~]# ip netns exec ns1 ip a 1: lo: <LOOPBACK> mtu 65536 qdisc noop state DOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 13: veth1@if12: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether fe:be:d8:2b:86:0c brd ff:ff:ff:ff:ff:ff link-netns ns0 inet 192.168.222.112/24 scope global veth1 valid_lft forever preferred_lft forever inet6 fe80::fcbe:d8ff:fe2b:860c/64 scope link valid_lft forever preferred_lft forever 从上面可以看出,我们已经成功启用了这个veth pair,并为每个veth设备分配了对应的ip地址。我们尝试在ns1中访问ns0中的ip地址:
[root@localhost ~]# ip netns exec ns1 ping 192.168.222.111 PING 192.168.222.111 (192.168.222.111) 56(84) bytes of data. 64 bytes from 192.168.222.111: icmp_seq=1 ttl=64 time=0.166 ms 64 bytes from 192.168.222.111: icmp_seq=2 ttl=64 time=0.081 ms 64 bytes from 192.168.222.111: icmp_seq=3 ttl=64 time=0.055 ms 64 bytes from 192.168.222.111: icmp_seq=4 ttl=64 time=0.075 ms 64 bytes from 192.168.222.111: icmp_seq=5 ttl=64 time=0.048 ms 64 bytes from 192.168.222.111: icmp_seq=6 ttl=64 time=0.059 ms ^C --- 192.168.222.111 ping statistics --- 6 packets transmitted, 6 received, 0% packet loss, time 5134ms rtt min/avg/max/mdev = 0.048/0.080/0.166/0.041 ms 可以看到,veth pair成功实现了两个不同Network Namespace之间的网络交互。
veth设备重命名
[root@localhost ~]# ip netns exec ns0 ip link set veth0 down [root@localhost ~]# ip netns exec ns0 ip link set dev veth0 name eth0 [root@localhost ~]# ip netns exec ns0 ifconfig -a eth0: flags=4098<BROADCAST,MULTICAST> mtu 1500 inet 192.168.222.111 netmask 255.255.255.0 broadcast 0.0.0.0 ether 16:4f:71:a9:27:41 txqueuelen 1000 (Ethernet) RX packets 19 bytes 1538 (1.5 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 20 bytes 1608 (1.5 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 10 bytes 840 (840.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 10 bytes 840 (840.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 容器的常用操作
查看容器的主机名
[root@localhost ~]# docker run -it --name b1 --network bridge --rm busybox / # hostname 0b0052dd49c5 在容器启动时注入主机名
[root@localhost ~]# docker run -it --name b1 --network bridge --hostname tushanbu --rm busybox / # hostname tushanbu / # cat /etc/hosts 127.0.0.1 localhost ::1 localhost ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters 172.17.0.2 tushanbu //注入主机名时会自动创建主机名到IP的映射关系 / # cat /etc/resolv.conf # Generated by NetworkManager nameserver 192.168.222.2 //DNS也会自动配置为宿主机的DNS / # ping www.baidu.com //可以尝试ping百度 PING www.baidu.com (182.61.200.6): 56 data bytes 64 bytes from 182.61.200.6: seq=0 ttl=127 time=24.784 ms 64 bytes from 182.61.200.6: seq=1 ttl=127 time=42.956 ms 64 bytes from 182.61.200.6: seq=2 ttl=127 time=57.581 ms 64 bytes from 182.61.200.6: seq=3 ttl=127 time=68.769 ms ^C --- www.baidu.com ping statistics --- 18 packets transmitted, 18 packets received, 0% packet loss round-trip min/avg/max = 22.958/47.448/75.551 ms 手动指定容器要使用的DNS
[root@localhost ~]# docker run -it --name b1 --network bridge --hostname tushanbu --dns 192.168.222.3 --rm busybox / # cat /etc/resolv.conf nameserver 192.168.222.3 手动往/etc/hosts文件中注入主机名到IP地址的映射
[root@localhost ~]# docker run -it --name b1 --network bridge --hostname tushanbu --add-host www.a.com:1.1.1.1 --rm busybox / # cat /etc/hosts 127.0.0.1 localhost ::1 localhost ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters 1.1.1.1 www.a.com 172.17.0.2 tushanbu 开放容器端口
执行docker run的时候有个-p选项,可以将容器中的应用端口映射到宿主机中,从而实现让外部主机可以通过访问宿主机的某端口来访问容器内应用的目的。
-p选项能够使用多次,其所能够暴露的端口必须是容器确实在监听的端口。
p选项的使用格式:
- containerPort: 将指定的容器端口映射至主机所有地址的一个动态端口
- hostPort:containerPort :将容器端口containerPort映射至指定的主机端口hostPort
- ip::containerPort :将指定的容器端口containerPort映射至主机指定ip的动态端口
- ip>:hostPort:containerPort: 将指定的容器端口containerPort映射至主机指定ip的端口hostPort
动态端口指的是随机端口,具体的映射结果可使用docker port命令查看。
[root@localhost ~]# docker run --name web --rm -p 80 nginx Unable to find image 'nginx:latest' locally latest: Pulling from library/nginx a2abf6c4d29d: Already exists a9edb18cadd1: Pull complete 589b7251471a: Pull complete 186b1aaa4aa6: Pull complete b4df32aa5a72: Pull complete a0bcbecc962e: Pull complete Digest: sha256:0d17b565c37bcbd895e9d92315a05c1c3c9a29f762b011a10c54a66cd53c9b31 Status: Downloaded newer image for nginx:latest /docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration /docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/ /docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh 10-listen-on-ipv6-by-default.sh: info: Getting the checksum of /etc/nginx/conf.d/default.conf 10-listen-on-ipv6-by-default.sh: info: Enabled listen on IPv6 in /etc/nginx/conf.d/default.conf /docker-entrypoint.sh: Launching /docker-entrypoint.d/20-envsubst-on-templates.sh /docker-entrypoint.sh: Launching /docker-entrypoint.d/30-tune-worker-processes.sh /docker-entrypoint.sh: Configuration complete; ready for start up 2022/08/10 04:26:58 [notice] 1#1: using the "epoll" event method 2022/08/10 04:26:58 [notice] 1#1: nginx/1.21.5 2022/08/10 04:26:58 [notice] 1#1: built by gcc 10.2.1 20210110 (Debian 10.2.1-6) 2022/08/10 04:26:58 [notice] 1#1: OS: Linux 4.18.0-257.el8.x86_64 2022/08/10 04:26:58 [notice] 1#1: getrlimit(RLIMIT_NOFILE): 1048576:1048576 2022/08/10 04:26:58 [notice] 1#1: start worker processes 2022/08/10 04:26:58 [notice] 1#1: start worker process 31 2022/08/10 04:26:58 [notice] 1#1: start worker process 32 2022/08/10 04:26:58 [notice] 1#1: start worker process 33 2022/08/10 04:26:58 [notice] 1#1: start worker process 34 以上命令执行后会一直占用着前端,我们新开一个终端连接来看一下容器的80端口被映射到了宿主机的什么端口上
[root@localhost ~]# docker port web 80/tcp -> 0.0.0.0:49153 80/tcp -> :::49153 由此可见,容器的80端口被暴露到了宿主机的49153端口上,此时我们在宿主机上访问一下这个端口看是否能访问到容器内的站点
[root@localhost ~]# curl http://127.0.0.1:49153 <!DOCTYPE html> <html> <head> <title>Welcome to nginx!</title> <style> html { color-scheme: light dark; } body { width: 35em; margin: 0 auto; font-family: Tahoma, Verdana, Arial, sans-serif; } </style> </head> <body> <h1>Welcome to nginx!</h1> <p>If you see this page, the nginx web server is successfully installed and working. Further configuration is required.</p> <p>For online documentation and support please refer to <a href="http://nginx.org/">nginx.org</a>.<br/> Commercial support is available at <a href="http://nginx.com/">nginx.com</a>.</p> <p><em>Thank you for using nginx.</em></p> </body> </html> iptables防火墙规则将随容器的创建自动生成,随容器的删除自动删除规则。
将容器端口映射到指定IP的随机端口
[root@localhost ~]# docker run --name web --rm -p 192.168.222.250::80 nginx /docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration /docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/ /docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh 10-listen-on-ipv6-by-default.sh: info: Getting the checksum of /etc/nginx/conf.d/default.conf 10-listen-on-ipv6-by-default.sh: info: Enabled listen on IPv6 in /etc/nginx/conf.d/default.conf /docker-entrypoint.sh: Launching /docker-entrypoint.d/20-envsubst-on-templates.sh /docker-entrypoint.sh: Launching /docker-entrypoint.d/30-tune-worker-processes.sh /docker-entrypoint.sh: Configuration complete; ready for start up 2022/08/10 04:33:11 [notice] 1#1: using the "epoll" event method 2022/08/10 04:33:11 [notice] 1#1: nginx/1.21.5 2022/08/10 04:33:11 [notice] 1#1: built by gcc 10.2.1 20210110 (Debian 10.2.1-6) 2022/08/10 04:33:11 [notice] 1#1: OS: Linux 4.18.0-257.el8.x86_64 2022/08/10 04:33:11 [notice] 1#1: getrlimit(RLIMIT_NOFILE): 1048576:1048576 2022/08/10 04:33:11 [notice] 1#1: start worker processes 2022/08/10 04:33:11 [notice] 1#1: start worker process 31 2022/08/10 04:33:11 [notice] 1#1: start worker process 32 2022/08/10 04:33:11 [notice] 1#1: start worker process 33 2022/08/10 04:33:11 [notice] 1#1: start worker process 34 在另一个终端上查看端口映射情况
[root@localhost ~]# docker port web 80/tcp -> 192.168.222.250:49153 将容器端口映射到宿主机的指定端口
[root@localhost ~]# docker run --name web --rm -p 80:80 nginx /docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration /docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/ /docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh 10-listen-on-ipv6-by-default.sh: info: Getting the checksum of /etc/nginx/conf.d/default.conf 10-listen-on-ipv6-by-default.sh: info: Enabled listen on IPv6 in /etc/nginx/conf.d/default.conf /docker-entrypoint.sh: Launching /docker-entrypoint.d/20-envsubst-on-templates.sh /docker-entrypoint.sh: Launching /docker-entrypoint.d/30-tune-worker-processes.sh /docker-entrypoint.sh: Configuration complete; ready for start up 2022/08/10 04:35:18 [notice] 1#1: using the "epoll" event method 2022/08/10 04:35:18 [notice] 1#1: nginx/1.21.5 2022/08/10 04:35:18 [notice] 1#1: built by gcc 10.2.1 20210110 (Debian 10.2.1-6) 2022/08/10 04:35:18 [notice] 1#1: OS: Linux 4.18.0-257.el8.x86_64 2022/08/10 04:35:18 [notice] 1#1: getrlimit(RLIMIT_NOFILE): 1048576:1048576 2022/08/10 04:35:18 [notice] 1#1: start worker processes 2022/08/10 04:35:18 [notice] 1#1: start worker process 31 2022/08/10 04:35:18 [notice] 1#1: start worker process 32 2022/08/10 04:35:18 [notice] 1#1: start worker process 33 2022/08/10 04:35:18 [notice] 1#1: start worker process 34 在另一个终端上查看端口映射情况
[root@localhost ~]# docker port web 80/tcp -> 0.0.0.0:80 80/tcp -> :::80 



