- A+
iptables、共享上网SNAT、端口转发DNAT
1.防火墙概述
封端⼝,封ip
实现NAT功能
共享上⽹
端⼝映射(端⼝转发),ip映射
2.防火墙
2.1防火墙种类以及使用说明
硬件:整个企业入口
软件:开源软件 网站内部 封ip
iptables
云防火墙
安全组
NAT网关
waf应用防火墙
2.2专有名词
容器、表、链、规则
2.3iptables执行过程
1.防⽕墙是层层过滤的,实际是按照配置规则的顺序从上到下,从前到后进⾏过滤的。
2.如果匹配成功规则,即明确表示是拒绝(DROP)还是接收(ACCEPT),数据包就不再向下匹配新的规则。
3.如果规则中没有明确表明是阻⽌还是通过的,也就是没有匹配规则,向下进⾏匹配,直到匹配默认规则得到明确的阻⽌还是通过。
4.防⽕墙的默认规则是所有规则都匹配完才会匹配的。
2.4表与链
iptables 是 4表伍链
4表: filter 表 nat表 raw表 mangle表
伍链: INPUT OUTPUT FORWARD PREROUTING POSTROUTING
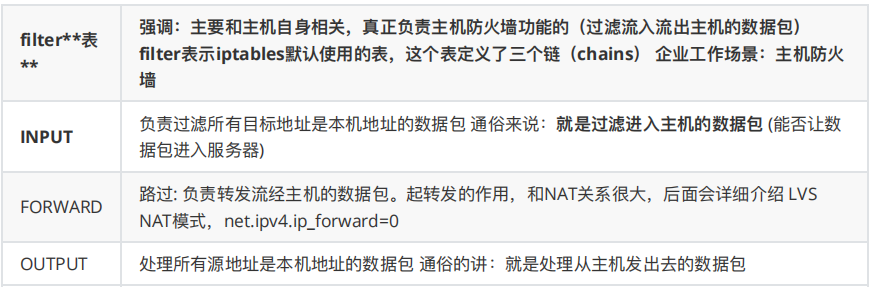
1.filter表
实现防火墙功能:屏蔽或准许端口ip
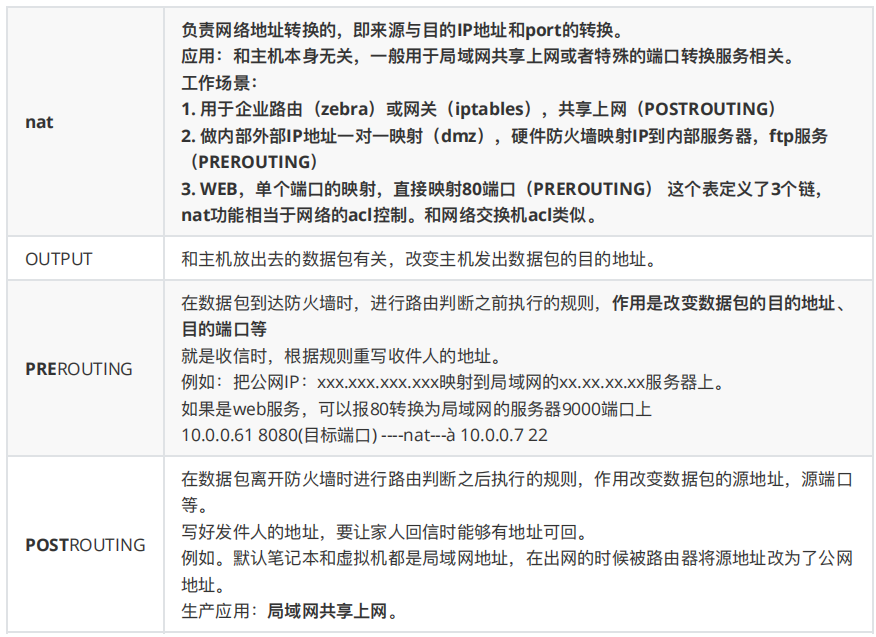
2.nat表
实现nat功能:实现共享上网 端口映射和ip映射
2.5环境准备及命令
先关闭防火墙
systmectl stop firewalld systemctl disable firewalld 1.安装并启动
yum install iptables-services systemctl enable iptables systemctl start iptables 2.设置开机自启防火墙相关模块
cat >>/etc/rc.local<<EOF modprobe ip_tables modprobe iptable_filter modprobe iptable_nat modprobe ip_conntrack modprobe ip_conntrack_ftp modprobe ip_nat_ftp modprobe ipt_state EOF lsmod | egrep 'filter|nat|ipt' 3.查看规则
iptables -nL 默认filter -n不要把端⼝ 或ip反向解析为名字 -L 列出规则
[root@localhost ~]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination 查看指定表的规则 iptables -t nat -nL
[root@localhost ~]# iptables -t nat -nL Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain INPUT (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination 配置filter表规则
| -A | 添加防火墙规则(尾部追加) |
|---|---|
| -D | 删除防火墙规则 |
| -I | 插入防火墙规则(首部插入) |
| -F | 清空防火墙规则 |
| -X | 删除用户自定义的链 |
| -L | 列出添加防火墙规则 |
| -R | 替换防火墙规则 |
| -Z | 清空防火墙数据表统计信息 |
| -P | 设置链默认规则 |
| -p | 协议 protocal tcp/udp/icmp/all 指定端口的时候需要用到指定协议 |
| --dport | 目标端口 |
| -j | 满足条件后的动作 DROP/ACCEPT/REJECT drop 把数据丢掉不会返回给用户 reject 返回拒绝信息 |
| -s | --source 源ip |
| -d | --destination ⽬标ip |
1.先清空规则
[root@localhost ~]# iptables -F [root@localhost ~]# iptables -X [root@localhost ~]# iptables -Z [root@localhost ~]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination 2.添加规则
iptables -t filter -I INPUT -p tcp --dport 22122 -j drop 3.删除规则
iptables -t filter -D INPUT 1 //1是行号 上述添加的规则的行号 1:封ip
1.192.168.70.133机器 ping 192.168.70.136机器
[root@web2 ~]# ping 192.168.70.136 PING 192.168.70.136 (192.168.70.136) 56(84) bytes of data. 64 bytes from 192.168.70.136: icmp_seq=1 ttl=64 time=0.937 ms 2.136机器添加规则
iptables -t filter -I INPUT -s 192.168.70.134 -j DROP 3.删除规则
iptables -D INPUT 1 //删除后可以发现又继续ping了 2:禁止网段访问指定端口
iptables -t filter -I INPUT -s 192.168.70.0/24 -p tcp --dport 8888 -j DROP 3:只允许指定网段连入
iptables -I INPUT ! -S 192.168.70.0/24 -j DROP 4:指定多端口
iptables -I INPUT -m multiport -p tcp --dport 80,433 -j DROP //禁止80和433端口 iptables -I INPUT -p tcp --dport 1:10 -j DROP //禁止1-10端口 5:控制是否能ping
iptables -I INPUT -p icmp -j DROP 另一种方法
vim /etc/sysctl.conf //添加如下一条指令 net.ipv4.icmp_echo_ignore_all = 1 sysctl -p //生效 6:匹配⽹络状态(TCP/IP连接状态)
NEW:已经或将启动新的连接
ESTABLISHED:已建⽴的连接
RELATED:正在启动的新连接INVALID:⾮法或⽆法识别的
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT 7:限制并发及速率
-m limit --limit 10/minute #每分钟只能有10个数据包 每6秒⽣成 8:防⽕墙规则的保存与恢复
iptables-save 默认输出到屏幕
iptables-restore 加上⽂件
写⼊到/etc/sysconfig/iptables
iptables-save > /etc/sysconfig/iptables iptables-restore < /etc/sysconfig/iptables 3.实际⽣产⽤法
iptables -F iptables -A INPUT -p tcp --dport 22 -j ACCEPT iptables -A INPUT -i lo -j ACCEPT iptables -A OUTPUT -o lo -j ACCEPT iptables -A INPUT -s 允许的IP地址 -j ACCEPT iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -P INPUT DROP iptables-save 4.共享上网SNAT
实现:内部网络的服务器通过可访问外网的机器访问到外网
环境准备
server01设置为VMnet2 192.168.100.18
server02设置为NAT 192.168.70.134 网络再添加一个网卡VMnet2 192.168.100.16
1.设置好server01的ip
[root@server01 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens33 BOOTPROTO="none" IPADDR=192.168.100.18 NETMASK=255.255.255.0 NAME="ens33" DEVICE="ens33" DNS1=114.114.114.114 2.设置好server02的ip
[root@server02 ~]# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:eb:13:88 brd ff:ff:ff:ff:ff:ff inet 192.168.70.134/24 brd 192.168.70.255 scope global noprefixroute dynamic ens33 valid_lft 5270229sec preferred_lft 5270229sec inet6 fe80::725c:49ee:6f78:42a0/64 scope link noprefixroute valid_lft forever preferred_lft forever 3: ens37: <BROADCAST,MULTICAST> mtu 1500 qdisc pfifo_fast state DOWN group default qlen 1000 link/ether 00:0c:29:eb:13:92 brd ff:ff:ff:ff:ff:ff [root@server02 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens37 BOOTPROTO="none" IPADDR=192.168.100.16 NETMASK=255.255.255.0 NAME="ens37" DEVICE="ens37" DNS1=114.114.114.114 [root@server02 ~]# systemctl restart network [root@server02 ~]# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:eb:13:88 brd ff:ff:ff:ff:ff:ff inet 192.168.70.134/24 brd 192.168.70.255 scope global noprefixroute dynamic ens33 valid_lft 5269237sec preferred_lft 5269237sec inet6 fe80::725c:49ee:6f78:42a0/64 scope link noprefixroute valid_lft forever preferred_lft forever 3: ens37: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:eb:13:92 brd ff:ff:ff:ff:ff:ff inet 192.168.100.16/24 brd 192.168.100.255 scope global noprefixroute ens37 valid_lft forever preferred_lft forever inet6 fe80::20c:29ff:feeb:1392/64 scope link valid_lft forever preferred_lft forever 3.测试ping相互下一
[root@server01 ~]# ping 192.168.100.16 4.server02开启转发功能
[root@serve02 ~]# echo 'net.ipv4.ip_forward = 1' >> /etc/sysctl.conf [root@serve02 ~]# sysctl -p 5.server02设置iptables
[root@serve02 ~]# iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -j SNAT --to-source 192.168.70.134 6.测试
[root@server01 ~]# ping baidu.com //能通则成功了 [root@server02 ~]# iptables -t nat -D POSTROUTING 1 //再试着关闭规则 再试试ping 5.端口转发DNAT
在上述snat基础上增加一台机器server03
1.server02添加prerouting规则
iptables -t nat -A PREROUTING -d 192.168.70.134 -p tcp --dport 9000 -j DNAT --to-destination 192.168.100.18:22 2.server03测试
[root@localhost ~]# ssh 192.168.70.134 -p 9000 root@192.168.70.134's password: Last login: Fri Sep 1 20:37:06 2023 [root@localhost ~]# ip a //查看端口可以发现连上的是server01 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:0c:29:18:39:18 brd ff:ff:ff:ff:ff:ff inet 192.168.100.18/24 brd 192.168.100.255 scope global noprefixroute ens33 valid_lft forever preferred_lft forever inet6 fe80::725c:49ee:6f78:42a0/64 scope link noprefixroute valid_lft forever preferred_lft forever 



